
Many jewelers are unaware of the risks associated with running outdated legacy software. This article explains the risks of on-prem systems in simple terms and equips you with the right questions to ask your provider in order to protect your business.
What is on-premise?
As the name suggests, on-premise or “on-prem” software is a type of software that is hosted on your business premises. It is sometimes referred to as “local” because is hosted locally.
On-premise software will require a dedicated computer on your business premises dedicated to actually running and serving the software program to other computers in your business. All other computers that you want to run the program are considered clients of the server computer and must be on the same local network (LAN).
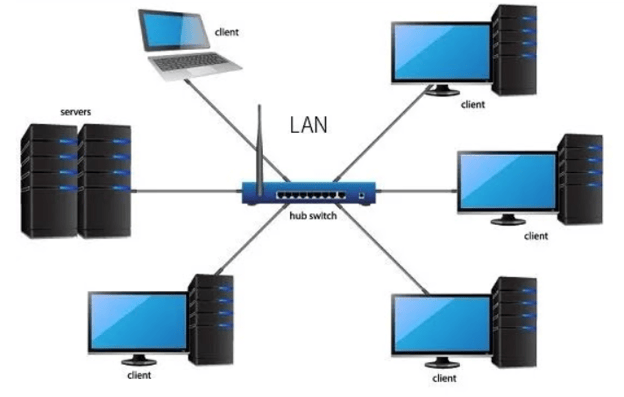
How do I know if my software is on-prem?
Here are a few indicators that you have a locally hosted system:
- can only be used on a computer, not a tablet or smartphone
- the computer needs to have certain “system requirements”
- a requirement to take regular “back-ups” for disaster recovery protocols
- a requirement to “upgrade” periodically
- reliance on an on-site or off-site “IT guy” that periodically asks you to buy new hardware (servers)
- sometimes your POS drops or slows down in a way that is frustrating for the business (local database constraints)
- difficult and slow when you want to integrate any other system or tool
- you can only access from your store or have to use a VPN
- you have something similar to this image under the stairs or in a back room or closet somewhere in your business:
What are the risks?
Four key risks relevant to on-prem software for jewelers:
- Hardware Failure
- Fire / Flood
- Being hacked
- Business continuity
Let’s explore these in more detail together:
1. Hardware Failure: This means the computer performing server duties has an unexpected failure, resulting in all other machines no longer being able to launch the program. If this is your Point of Sale system this may mean you cannot effect a sale in your store for the duration of the outage. This type of failure is inevitable in all computer hardware, it is just a question of time.
2. Fire / Flood: This means physical damage occurs to the computer performing server duties, interrupting operations and a loss of business critical data . A common example is someone inadvertently spills liquid on the machine or there is a small “melting” event caused by insufficient ventilation.
3. Being Hacked: This means a targeted attack on your computer system by a competitor or criminal. An example of a competitive attack would be your competitor down the road hiring a hacker to gain your hard-earned customer list and buying history. An example of ransom is the theft of customers’ personal data, resulting in reputational damage for the business unless a ransom is paid to the hackers.
4. Business Continuity: On-prem POS dropped below 50% market share in North America in 2022 and at the current rate of decline will be consigned to history in the coming decade.
Source: Forbes
The owners of your on-prem service are software professionals. They know the era where they have prospered is drawing to a close, and they are directly motivated to slow down your transition to more modern solutions. These companies are unlikely to have a credible succession plan and at some point will inevitably wind down their operations. Your business will be left with a system that belongs to a company that is no longer trading.
| Risk | Impact Level | Risk Level | Mitigation |
| Hardware Failure | Medium | Medium | regular monitoring & replacement of hardware |
| Fire / Flood | High | Low | Switch to a cloud-based system (no back-ups required, no hardware) |
| Being Hacked | High | High | Switch to a cloud-based system (servers in Microsoft/Google/Amazon data centers - which run all cloud-based services - have the strongest security perimeter in the world) |
| Business Continuity | High | High | Switch to a cloud-based system (servers in Microsoft/Google/Amazon data centers - which run credible cloud-based services) |
So why is my current provider telling me the cloud is dangerous?
It is a question of vested interests: unless they can evolve their services to cloud-based services, they stand to lose your business IF they admit cloud-based is the future. The unfortunate reality for most of these companies is that cloud-native skills are very different from those required for legacy systems and it would involve a total replacement of their existing workforce. Even if they are willing to undertake such a drastic change to their companies, cloud-native capabilities are in hot demand and qualified talent would be very unlikely to want to join an old-fashioned company when they have a long list of modern suitors to choose from.
Finally, consider this: In order for their claim that the “cloud is dangerous” to be right, all leading software firms - names like Microsoft, Google, Amazon, SAP, and Oracle - have to be wrong. These companies have all publicly declared the cloud is the only way they will operate going forward and have either deprecated or are in the process of deprecating legacy on-premise solutions. For example, in 2016 SAP announced it will no longer support customers on-premise solutions after 2024.
What they are not telling you
Your on-premise provider will tell you that “the internet is not safe” and that “you are safer keeping your data in your own hands”. This is dangerously misleading because the reality is that at the back of the server in your building is an ethernet cable with a blinking green light. This is how your business connects to the internet; any risks associated to being on the internet are being run by your local server. In other words, the blinking green light means the cloud is in your building, even if you run on-prem software.
How to protect your business
The way to mitigate this risk is to measure and understand the strength of your network perimeter. The mechanism to measure this is a regular penetration test (performed by professional security testing companies) that will expose your vulnerabilities. Each vulnerability should be addressed in order for it not to show up on the next test, which requires your company or provider to dedicate many hours of expensive software engineers’ time to remedy each and every issue on an ongoing basis.
As each test normally costs in excess of $5k, plus many times that in engineering costs to address the resulting vulnerabilities, it can quickly get expensive in local area networks. By contrast, the great advantage of cloud-based systems means it is one larger network, which can be tested centrally by the provider, who can absorb the cost of both the tests and the remedy because it is amortized over many customers. This delivers a win-win for both provider and customer that is impossible for on-premise era companies to compete with - both from a security standpoint and from a cost standpoint…
Summary
The cloud is not actually in the sky, it’s very much down on the ground - in places like Utah or Nevada where competent professionals are dedicated to service uptime, incident response, and world-class security.
It is not cloud unless:
- you can access from anywhere
- can use on any device that has access to the internet (eg your smartphone)
- you pay a monthly subscription
- you never get told you need to “upgrade” to a new version for reason X,Y or Z
- you don’t need to buy any specific hardware
If you use cloud services, you will quickly ask yourself why you tolerated on-premise solutions for so long. Most industries made this transition 5-10 years ago, our industry is one of the last bastions for on-prem software. This article seeks to provide all the insight and nuance necessary for you to make an informed decision about your business’s transition to cloud-based operations.
How can you validate the claims made in this article?
You can contact your on-premise service provider and ask simple questions such as:
- Q1: If the internet is so full of risk, can you explain to me how you can justify the green blinking light at the back of the server on my premises please?
- Answer will likely be about their great security and why you don't need to be
- Subsequent question: move to Q2
- Q2: Can you explain to me how my data is safer in the servers you have set up for me, compared to an industry-leading data center run by Microsoft or Google?
- Answer will likely be fear-based, “alluding to big tech spying on you OR your data will be productized”
- Q3: Do you conduct regular penetration tests on my servers & my network?
-
- Answer is likely no, or “you should do that yourself” meaning they are not interested in your perimeter defense - and so should not be claiming they are in any way a safe place to store your data
- If the answer is yes, a follow-up question would be:
- Q: Can I see the results of the most recent test? I would like to know what vulnerabilities were uncovered and what steps you took to address them?



